What Makes Bootable Containers Different from Traditional Containers?
We all know containers run on top of an operating system. But what if the container itself could be the operating system? That’s the idea behind bootable containers.

If you’ve used containers before, you already know how much they’ve changed the way we build and run apps. Tools like Docker and Kubernetes made packaging and deploying software simpler than ever. But there’s another step forward you might not have seen yet: bootable containers.
The Container Recap
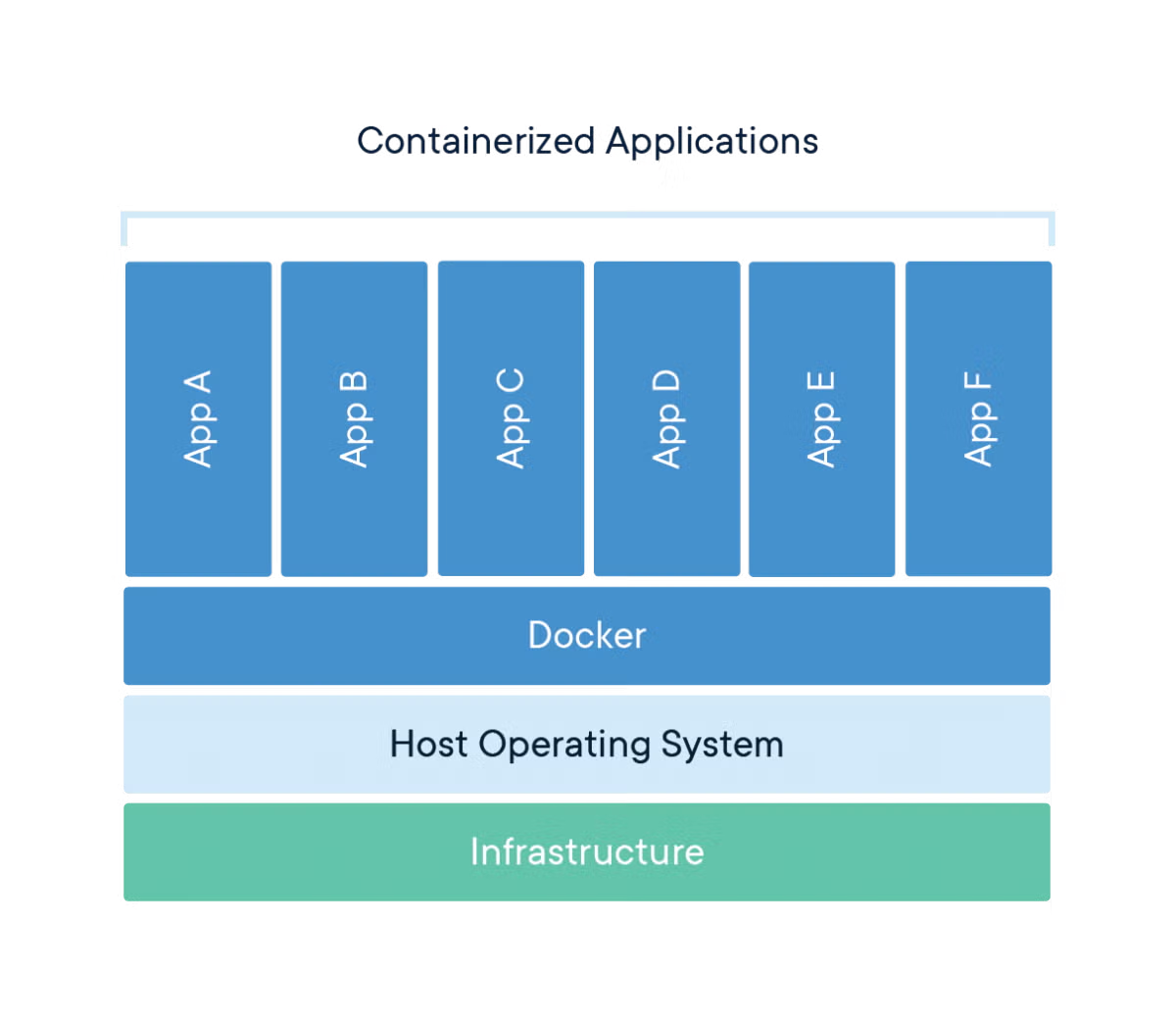
Traditional containers work by sharing the host's kernel while providing isolated userspace environments for applications. When you run a Docker container, you're essentially starting a segregated process on your host OS with its own filesystem, network interfaces, and process tree. The container runtime manages these containers on top of your existing operating system.
What Makes Bootable Containers Different?
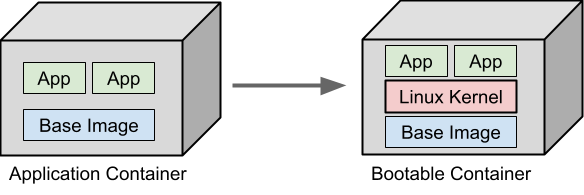
Bootable containers flip this model on its head. Instead of running on top of an existing OS, they become the OS. A bootable container is packaged using container technologies but is designed to boot directly on bare metal or in a virtual machine.
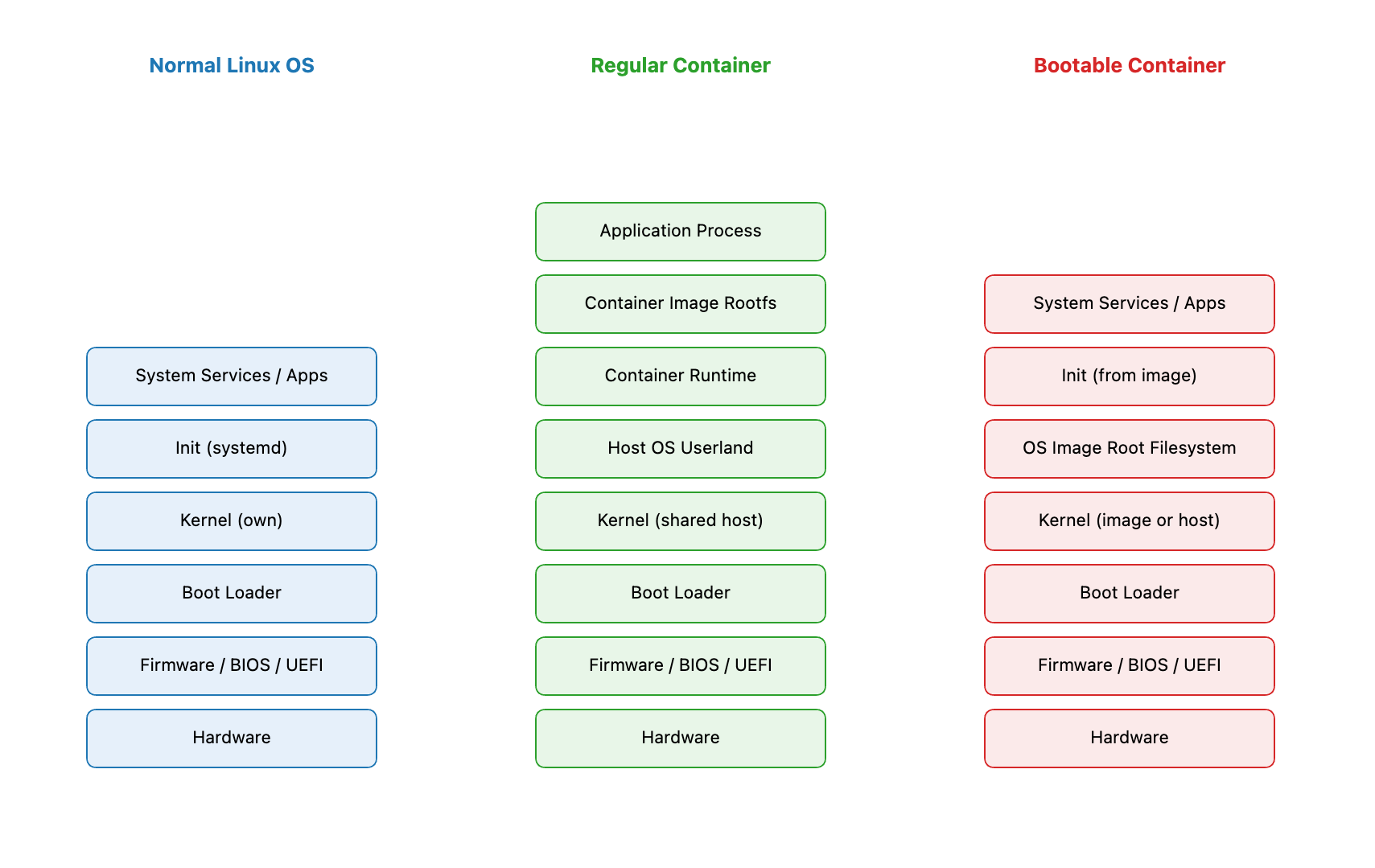
Bootable Containers vs. Traditional Linux OS
| Aspect | Traditional Linux OS | Bootable Containers |
|---|---|---|
| Update Mechanism | Package-by-package with package manager | Atomic, image-based updates |
| Configuration | Often diverges between systems | Consistent across fleet |
| Filesystem | Mutable, changes in place | Immutable root filesystem |
| Installation | Unique per machine | Identical images across all systems |
| Customization | Ad-hoc changes on running system | Image rebuilding with version control |
| Rollbacks | Complex, often manual | Simple, atomic image rollback |
| Footprint | Often includes unnecessary packages | Minimal, purposefully designed |
| Security Profile | Larger attack surface | Reduced attack surface |
With traditional OS, you typically install a base system and then modify it over time with package managers. Each system tends to evolve independently, leading to "configuration drift" where supposedly identical systems have subtle differences that cause problems.
| Feature | Traditional Linux | Regular Containers | Bootable Containers |
|---|---|---|---|
| Execution | Direct on hardware | On host OS | Direct on hardware |
| Kernel | Own kernel | Shared host kernel | Own kernel |
| Updates | Package manager | Image replacement | OS image replacement |
| Isolation | None (full system) | Process/filesystem isolation | None (full system) |
| State | Stored on local disk | Ephemeral or volumes | Separate data volumes |
| Packaging | RPM/DEB packages | Container images | Container images |
| Boot Process | Traditional boot loader | Container runtime | Boot loader to container |
| Ideal For | General purpose | Application deployment | Infrastructure as code |
| Management | Configuration management | Container orchestration | Image-based orchestration |
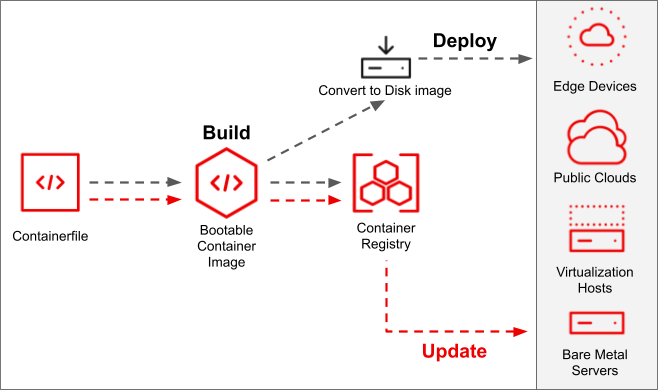
Bootable containers, on the other hand, treat the operating system as an immutable artifact. Rather than updating packages in place, you replace the entire OS image when updates are needed, ensuring consistency across your infrastructure.
Open Source Projects
Several projects are making bootable containers accessible:
1. bootc
bootc is Red Hat's initiative for creating bootable containers. It enables:
- Direct booting of OCI container images as the host OS
- Integration with Fedora and RHEL ecosystems
- Standardized approach to bootable containers
- Simple transactional updates and rollbacks

2. LinuxKit
Created by Docker, LinuxKit is a toolkit for building custom operating systems that run containers. It offers:
- Modular approach to OS building with containers
- Security-first design philosophy
- Minimal base with just what you need
- Ability to target multiple platforms including cloud and IoT

3. Other Notable Projects
- Flatcar Container Linux: A community-driven immutable Linux distribution forked from CoreOS
- AWS Bottlerocket: AWS's minimal OS designed specifically for running containers
- Fedora CoreOS: Red Hat's immutable OS combining the best of CoreOS and Project Atomic
- Talos Linux: Kubernetes-focused OS built from container images.
What are the Use Cases?
1. Edge Computing at Scale
Scenario: A telecommunications company managing thousands of edge computing nodes across multiple countries.
Solution: Using bootable containers allows them to:
- Deploy identical OS environments to all edge nodes
- Update the entire fleet with a single tested image
- Rollback problematic updates with a simple reboot
- Reduce edge device management overhead
2. Hybrid Cloud Consistency
Scenario: An enterprise running workloads across on-premises data centers, AWS, and Azure.
Solution: Bootable containers provide:
- The same base OS across all environments
- Consistent behavior regardless of underlying infrastructure
- Simplified compliance and security auditing
- Reduced "works in my environment" issues
3. IoT Fleet Management
Scenario: Smart manufacturing deployment with hundreds of specialized devices on the factory floor.
Solution: Bootable containers deliver:
- Reliable, atomic updates to all devices
- Minimal OS footprint for resource-constrained devices
- Automatic rollback if devices fail to come online after update
- Unified management plane for the entire fleet
4. Security-Focused Operations
Scenario: Financial services company with strict security requirements.
Solution: Bootable containers enhance security through:
- Reduced attack surface with minimal OS components
- Immutable infrastructure preventing runtime modifications
- Cryptographically verified OS images
- Consistent security controls across all systems
Summary
Bootable containers reduce configuration drift, shrink the attack surface, and let you manage OS updates much like application releases. They’re especially useful for edge fleets, IoT, cloud-native node images, and security-sensitive environments.
Bootable containers package an entire operating system as an immutable, container-style image that can boot directly on hardware or in a VM. Unlike regular containers that depend on a host OS and share its kernel, bootable images become the OS: they provide a minimal, consistent runtime, atomic updates, and simple rollbacks.





